SS7 access is a critical component of telecommunications that has been the subject of much discussion and concern over the years. This article aims to delve deep into the intricacies of SS7 (Signaling System No. 7), its functionality, security implications, and the ongoing debates surrounding its use in modern communication networks. By the end of this article, you will have a thorough understanding of SS7 access and its significance in the telecommunications landscape.
The significance of SS7 access cannot be overstated, as it plays a vital role in ensuring seamless communication between mobile networks, routing calls, and managing mobile services. However, with its importance comes a plethora of security vulnerabilities that can be exploited by malicious actors. This guide will provide insights into how SS7 works, its applications, and the potential risks associated with it, allowing readers to grasp both its advantages and drawbacks.
As we navigate through this complex topic, we will address various aspects of SS7 access, including its technical workings, the challenges it faces, and recommendations for improved security measures. Whether you're a telecommunications professional, a tech enthusiast, or simply curious about the topic, this comprehensive guide will serve as a valuable resource.
Table of Contents
- What is SS7?
- How SS7 Works
- Applications of SS7
- Security Issues with SS7
- Historical Context of SS7
- Future of SS7
- Best Practices for SS7 Security
- Conclusion
What is SS7?
SS7, or Signaling System No. 7, is a set of protocols used in public switched telephone networks (PSTN) and mobile networks to facilitate the exchange of information between network elements. Developed in the 1970s, SS7 provides a standardized method for signaling and controlling telephone calls, enabling various services such as call setup, routing, and teardown.
Key Features of SS7
- Signaling: It allows communication between different network components.
- Call Management: SS7 manages call setup, maintenance, and teardown.
- Number Translation: It supports services like toll-free numbers and local number portability.
- SMS Services: SS7 is essential for delivering text messages between mobile devices.
How SS7 Works
The SS7 architecture comprises various components, including signal transfer points (STPs), service control points (SCPs), and more. These components work together to ensure efficient communication between different networks.
The SS7 Protocol Stack
The SS7 protocol stack consists of several layers, including:
- Message Transfer Part (MTP): Responsible for message routing.
- Signaling Connection Control Part (SCCP): Provides additional routing capabilities.
- Transaction Capabilities Application Part (TCAP): Facilitates database queries and responses.
- Mobile Application Part (MAP): Manages mobile network services.
Applications of SS7
SS7 has a wide range of applications in the telecommunications sector, enhancing both user experience and network efficiency. Some key applications include:
- Call Routing: Ensures calls are directed to the correct destination.
- Mobile Roaming: Enables users to make and receive calls while traveling internationally.
- SMS Delivery: Facilitates the sending and receiving of text messages.
- Number Portability: Allows users to retain their phone numbers when switching carriers.
Security Issues with SS7
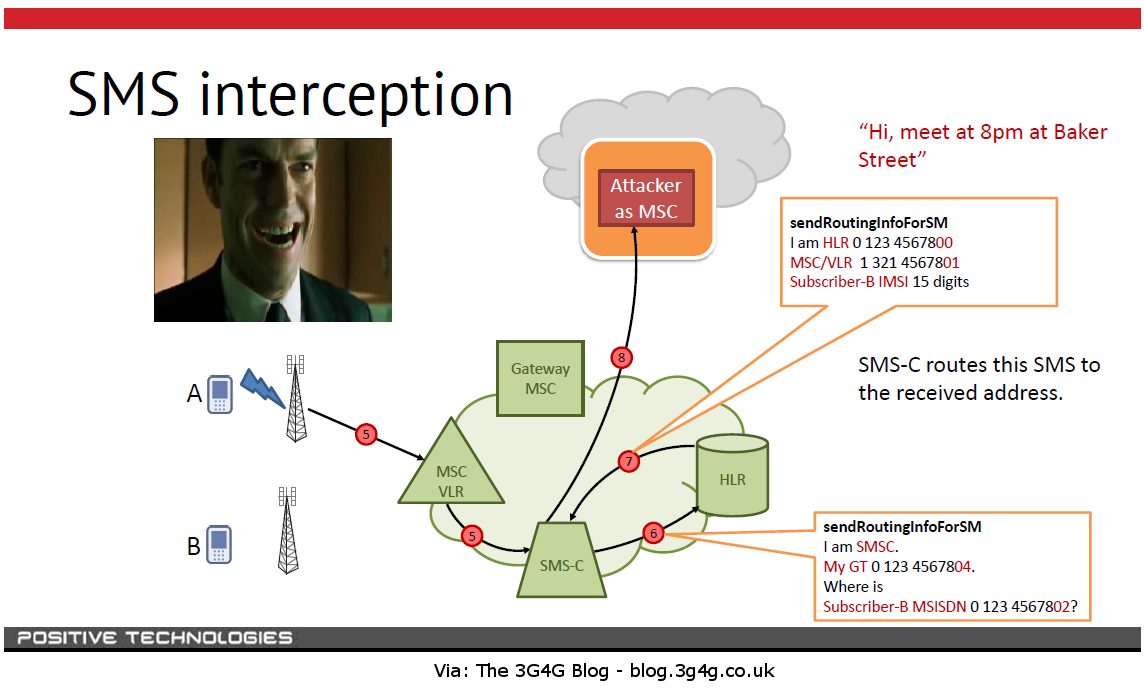
Despite its importance, SS7 is not without vulnerabilities. Cybersecurity experts have raised alarms about potential risks associated with SS7 access, leading to unauthorized surveillance and interception of communications.
Common Security Threats
- Call Interception: Attackers can listen in on calls.
- SMS Spoofing: Malicious actors can send fake messages.
- Location Tracking: SS7 can be exploited to track users' locations.
- Denial of Service: Attacks can disrupt network services.
Historical Context of SS7
Understanding the historical context of SS7 is essential for grasping its evolution and the challenges it currently faces. SS7 was first introduced in the late 1970s, primarily to improve call setup times and reduce the burden on circuit-switched networks.
Over the years, as mobile technology advanced, SS7 adapted to support new services, including SMS and mobile data. However, the proliferation of mobile devices has also opened up new avenues for exploitation, making security a pressing concern.
Future of SS7
As technology continues to evolve, so too must SS7. The future of SS7 will likely involve integrating new security protocols and transitioning towards more secure alternatives, such as Diameter, which is designed to address the shortcomings of SS7.
Best Practices for SS7 Security
To mitigate the risks associated with SS7 access, telecommunications providers must adopt best practices for securing their networks. Some recommended strategies include:
- Implementing Firewalls: Use firewalls to restrict unauthorized access to SS7 networks.
- Monitoring Traffic: Continuously monitor signaling traffic for unusual patterns.
- Adopting New Technologies: Transitioning to more secure signaling protocols.
- Employee Training: Educating staff about potential security threats and best practices.
Conclusion
In conclusion, SS7 access is a fundamental aspect of modern telecommunications, enabling critical services while also presenting significant security risks. Understanding how SS7 works, its applications, and the associated vulnerabilities is essential for both industry professionals and consumers alike.
As we move forward, it is crucial to prioritize security measures to safeguard against potential threats. We encourage readers to share their thoughts on SS7 access, its implications, and any additional insights they may have in the comments section below. Don't forget to explore our other articles for more information on telecommunications and cybersecurity!
Thank you for reading, and we hope to see you back on our site for more insightful content!
Article Recommendations
- Clr Soak Overnight
- Ruben Roman
- Legal Seafood Recipes Crab Cakes
- Outdoor Propane Heater Table Top
- Bryan Hearne
- Wallet With Pull Tab
- Jennifer Syme Crash
- Nina Aoulik
- How Old Is Adriana Lima 2024
- How To Make Raphael In Infinite Craft